A new ransomware is sweeping the globe, but there's a vaccine

It's a familiar story: You boot up your computer only to find a mysterious message saying your files are encrypted. You soon realize that your data is likely gone for good — even if you fork over a cryptocurrency ransom payment.
But this time around, as a new and virulent form of ransomware dubbed NotPetya sweeps the globe, it doesn't have to be this way.
Because this time around, there's a vaccine.
What is NotPetya?
The first symptoms of the attack appeared on June 27 in Ukraine, with the National Bank of Ukraine and the Kiev International Airport both hit hard. Even Chernobyl's radiation monitoring system has reportedly been affected. But NotPetya, which targets the Windows operating system, didn't stay there. Microsoft has confirmed that computers in 64 additional countries have been infected.
The ransomware, so called because it demands a payment from users in exchange for decrypting their files, appears to use some code from an earlier ransomware known as Petya. However, this latest version looks to have been souped up with the allegedly stolen NSA exploit EternalBlue — the same exploit that drove the spread of WannaCry — and as such has security researchers calling it "NotPetya."
SEE ALSO: It won't be easy for WannaCry hackers to get their cash
According to the security firm Symantec, NotPetya is particularly nasty because instead of just encrypting a system's files, it actually modifies a computer's master boot record in order to encrypt its hard disk.
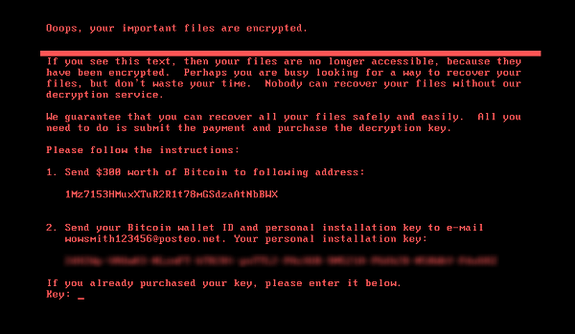
Image: symantec
Once a system is infected, a message is displayed demanding $300 worth of Bitcoin in exchange for a decryption key. However, as the listed email address for confirming that the ransom has been paid has been shut down by the email provider, there is little-to-no chance a decryption key will be provided even if a victim pays.
Essentially, those hit by NotPetya can kiss their data goodbye.
The vaccine
But the situation isn't hopeless. Those who either don't want to or simply can't afford to turn off their computer and wait for this all to blow over have a weapon in the battle against this attack. And, thankfully, it's a pretty simple home remedy.
A security researcher by the name of Amit Serper appears to have found a way to prevent the ransomware from running on vulnerable computers with just a few easy steps.
98% sure that the name is is perfc.dll Create a file in c:\windows called perfc with no extension and #petya #Nopetya won't run! SHARE!! https://t.co/0l14uwb0p9
— Amit Serper (@0xAmit) June 27, 2017
His observation, which has since been confirmed by other researchers, is that NotPetya looks for a specific file on a computer before encrypting the computer's contents. If that file is located, the ransomware won't proceed.
So all concerned users have to do is create a file by that name, and then NotPetya won't run. To do this, head to the C:\Windows folder and make a read-only file by the name of "perfc." Importantly, this should not have a file extension. Bleeping Computer has a great step-by-step guide for those looking for detailed instructions.
An added dose of security, which everyone should have done by now but clearly hasn't, is to install Windows security updates. The EternalBlue exploit used by NotPetya, which relies on a Server Message Block (SMB) vulnerability, was patched back in March.
Both keeping your Windows OS up to date with security patches, and creating the perfc file as explained by Serper, should be enough to vaccinate otherwise healthy computers against NotPetya. While that doesn't help the National Bank of Ukraine this time around, it may be enough to save you.
As for the next wave of ransomware? While predicting what's coming down the pike is a difficult if not impossible task, you can still take precautionary steps: Make sure your system is up to date, and be skeptical of any and all emails and links.
WATCH: Step inside the secretive class that turns people into hackers



